Let’s be honest right from the start:
Do you remember every single password you’ve ever created?
Do you remember every single platform you’ve signed up for?
Do you use a new, unique, long password for every application every single time?
If you answered all three questions with a resounding “yes”: congratulations and well done! If you had to answer at least one question with a “no”, you belong to the species of “common user”. A class of users who have long lost their way in the jungle of logins, forgetting the mail addresses and corresponding passwords to their applications and without any means of keeping track of it all.
In 2017, the average German user has gathered a whopping 78 different online accounts – a number set to increase even further.
Since we’re surfing the internet so frequently, we have an increasingly hard time efficiently organising the plethora of user names and passwords.
To be on the safe side, users would have to choose a unique password for each account they create. But as humans are lazy creatures by nature, prioritising comfort over security, they just use simpler passwords repeatedly on different platforms. In doing so, they make their lives easier and improve their user experience – for the moment.
Data piracy + cracked password = the worst user experience
This reckless behaviour makes it easier for cyberpunks to access the users’ accounts. The hacker’s success opens the door to multiple accounts – the result of comfortably using the same passwords over and over again. All of a sudden, bank accounts, online shops, dating platforms, mailboxes and many more are available. A complete stranger can confirm incoming verification mails, having access to the email account in question, and thus misuse sensitive data like credit card information while at the same time exchanging the old passwords with new ones. The users lose access to their personal accounts, their data and, in the worst case possible, a lot of money. This situation turns users into victims of the worst user experience possible – which they themselves are yet somehow responsible for. The users’ frustration is immense and their trust in the platform severely shaken. So what can we as user experience (UX) designers do to make others feel safe to use our service without worries?
If you want to check whether your credentials have already been stolen during a so-called data breach on a platform, just click on this button:
Two-Factor Authentication to strengthen security
In order to make the login process safer, some platforms already have started using two-factor authentication (2FA). This means that in addition to the password, the users have to confirm a so-called second factor (another kind of identity verification) before being able to log in. These two factors are a combination of something the users know (e.g. a password) and something they have (e.g. a code provided on a mobile app) or are (e.g. a fingerprint). This procedure has the advantage of providing safe platforms thanks to an active use of 2FA – even if users fall victim to stolen credentials.
At first glance, 2FA is another step and thus an additional hurdle for users to overcome on their path to a successful authentication. As UX designers, it is our job to protect users from any kind of irritation, keeping the application as simple as possible. This might sound contradictory to 2FA at first – but as usual, it depends on the correct assessment and decision. While this type of authentication is an additional step that reduces interaction speed, it still is a key factor for a positive user experience which helps customers safely navigate all their applications. In the long run, 2FA provides the better user experience.
The right way of offering 2FA
The mistake many platform providers make lies in the lack of combination of factor categories. In order to provide a more stable system, you should mix up at least two factors, each belonging to different categories.
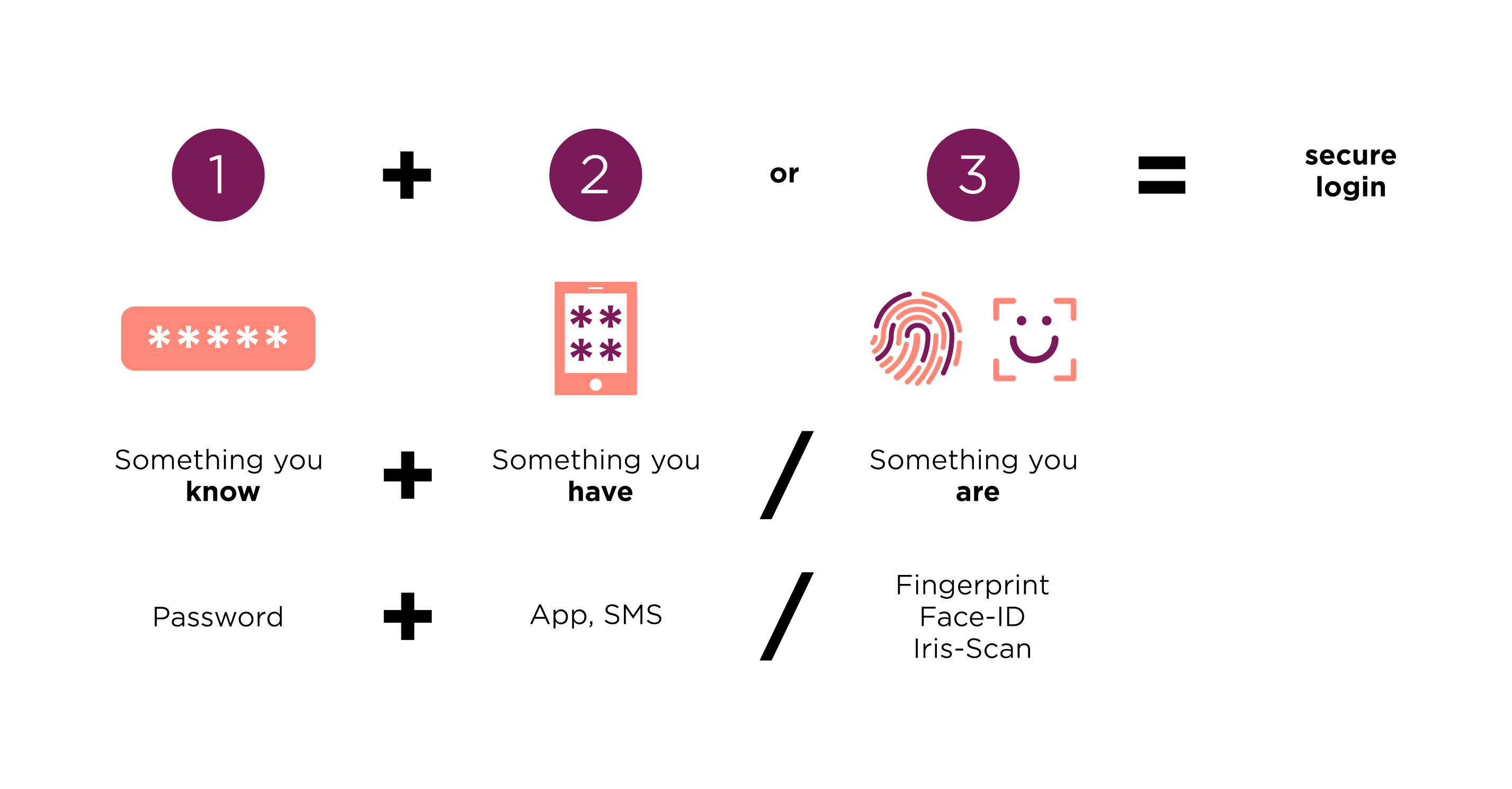
While several mechanisms come to mind when thinking about a second factor from the categories “something you have” and “something you are”, not every kind of authentication can score equally high in usability as well as security. As UX designers, we face a classic impasse between making an app’s use easy and safe at the same time. If one wins, the other suffers and vice versa. Obviously, a second step disturbing the login flow is not ideal – but falling victim to a hacker attack is a far worse user experience.
The Authenticator App and biometric data
We have evaluated the most important second factors for the login process from a UX designer’s perspective and turned the results into this table:
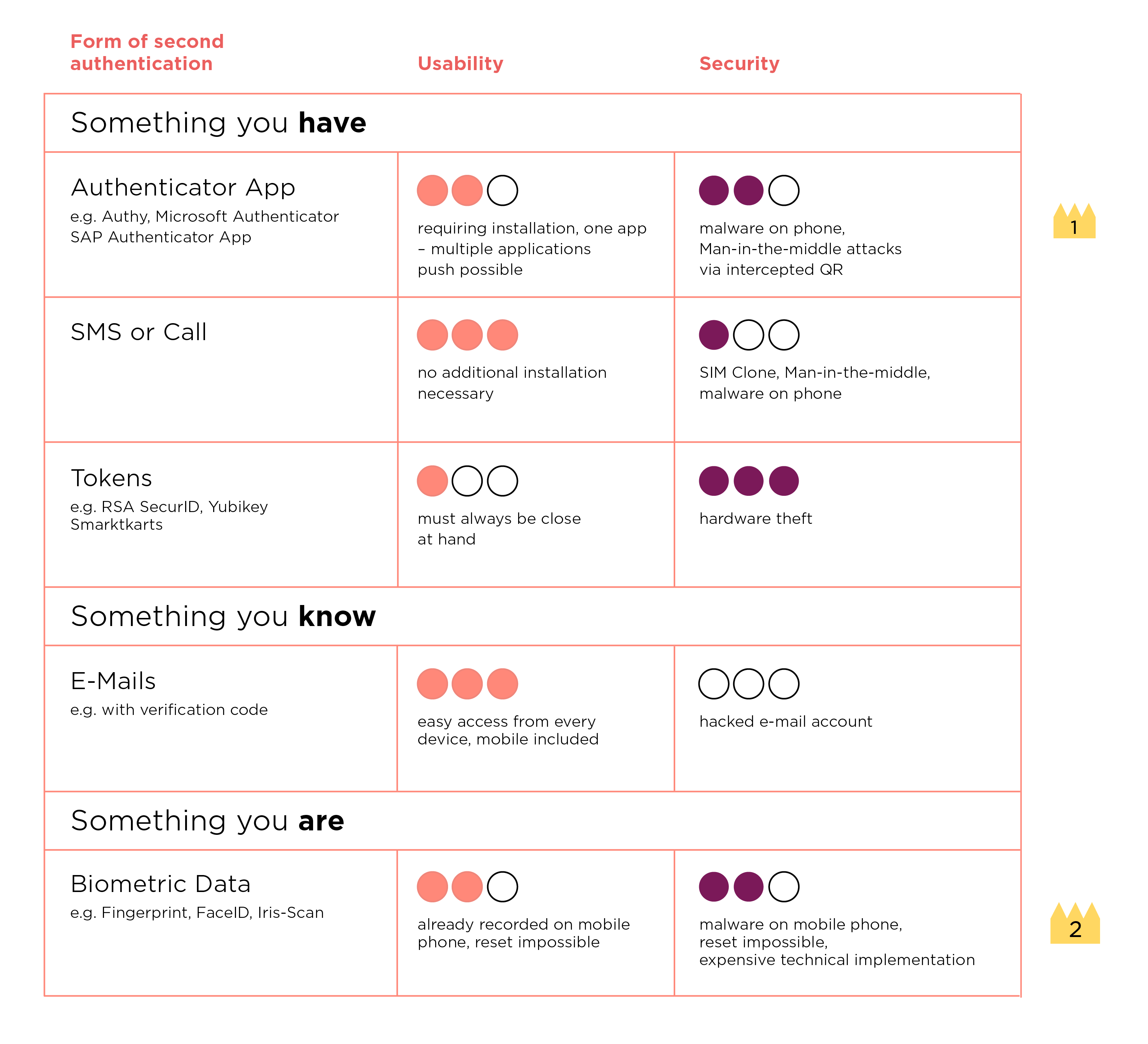
A good compromise between usability and security lies in using an authenticator app, available in many different variations. Their most practical feature: a single app can provide multiple platforms with so-called time-based one-time password (TOTP) codes. As a result, users only need one app for all their platforms. The codes are on display for a limited amount of time (usually several seconds) during which they are valid as verification on the respective platform, thus enormously lowering the danger of a hacker login.
Another valid second factor from a UX point of view consists in using biometric data. More often than not, users already registered their fingerprints on their laptops or their facial features on their mobile phones. This makes it easy for those data to be used for authentication. The technical implementation of browser-based logins, however, does pose a challenge. We have to continually wonder about things like “If my biometric data were stolen, how could I reset my face or fingerprint?”.
Biometric data is not „unhackable“, proven by the famous example of Wolfgang Schäuble’s fingerprint:
7 UX-pointers you should take to heart for a better integration of 2FA:
- Provide a good password policy
2FA does not compensate for a safe password which users have to choose first. Make sure they follow the correct password policy: unique, not used for another platform, a minimum of eight characters in length and a combination of letters (uppercase as well as lowercase), digits and special characters. Furthermore, it must not be a dictionary word. - Promote 2FA activation within the registration process
Integrate 2FA as an additional option when registering. If the users have time to spare, they can directly enable it. If they don’t, they at least are aware of its existence and can be pointed to where they can enable it later. - Offer 2FA on a voluntary basis
Provide the option of enabling 2FA or not (if those in charge of security give their consent to do so) while highlighting the advantages of 2FA in a transparent way. Ideally, a modal points out the option to the users yet again when they are using the service for the next time. - Use 2FA as a possible profile setting
Users should have the option of enabling 2FA in their profile settings. - Offer a variety of 2FA methods
By providing a small selection of different 2FA methods, users can choose the most comfortable one for themselves. Don’t offer more than two or three methods, however, in order to avoid a possible overload of choices. - Offer backup codes
Stress the importance of recovery/backup codes. Give users a clear, visual signal indicating that these codes are vital and that really printing them on a sheet of paper is a really good idea. The “Next” button should be inactive until the users click on “Print” or “Save”. - Enable device deactivation
Users should be able to disconnect devices already using 2FA, e.g. in case of a theft. It is crucial that 2FA can be deactivated either by using the old device (if not stolen) or backup codes, not by security questions or the password. It would defy the sense of 2FA if you could just outmanoeuvre it with the first factor. Please take into account the danger of social engineering attacks: make sure the personal verification process is implemented correctly. It’s no use promoting 2FA if hackers can turn into activated users simply by being asked for an address or their date of birth on the phone.
Conclusion
The safe use of web applications is a central part of a good user experience, which is why it should be the focal point of the design process.
Those devoted to security continuously find themselves faced with the sobering realisation that there is no absolute security. According to security expert Gene Spafford, “The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards”.
Still, 2FA offers a greater security compared to a simple password inquiry since the combination of multiple factors makes it harder for attackers to hack an account. Especially automated attacks can be prevented much better this way.
Despite that, 2FA does come with some risks: If attackers enter a user name and a password on a platform and the result is a 2FA screen popping up, they know the data is correct. If they move on to the next, 2FA-less platform, personal data is easy prey. Therefore, a safe, unique password is much more significant than any later try to make authentication more secure – a fact that most users are not aware of. On one hand, 2FA provides a dangerously comfortable feeling which lulls users into a false sense of security, resulting in them choosing a weak password. On the other hand, even if the security of individual factors is lacking, the combination of weak factors is still more stable than one strong factor on its own. Yet another point in favour of 2FA.
In conclusion, you have to choose authentication with several factors deliberately. Before starting to work on the UX design, you should weigh up pros and cons as well as determine a strong password policy for registration. Only then can users receive maximum protection, which in turn raises their trust in the platform.
Where things will go from here – a glimpse into the future?
The next step to make the users’ lives easier is using single sign-on (SSO), a scheme including 2FA which is already in use in many areas. Users verify once, gaining access to several services and resources. This in turn brings with it a significant decrease in logins. From a UX point of view, setting up SSO is only beneficial since both user experience as well as security increase.
A glimpse into the future looks quite exciting: there is a strong tendency to invisible multi-factor authentication that doesn’t need an active user and thus is undisturbed in its flow. A possible application scenario could be an automatic matching of two devices within the same room, a process called “ambient sound”. The trend certainly goes towards automated but safe processes that free users from an everlasting barrage of passwords. Phew, finally.